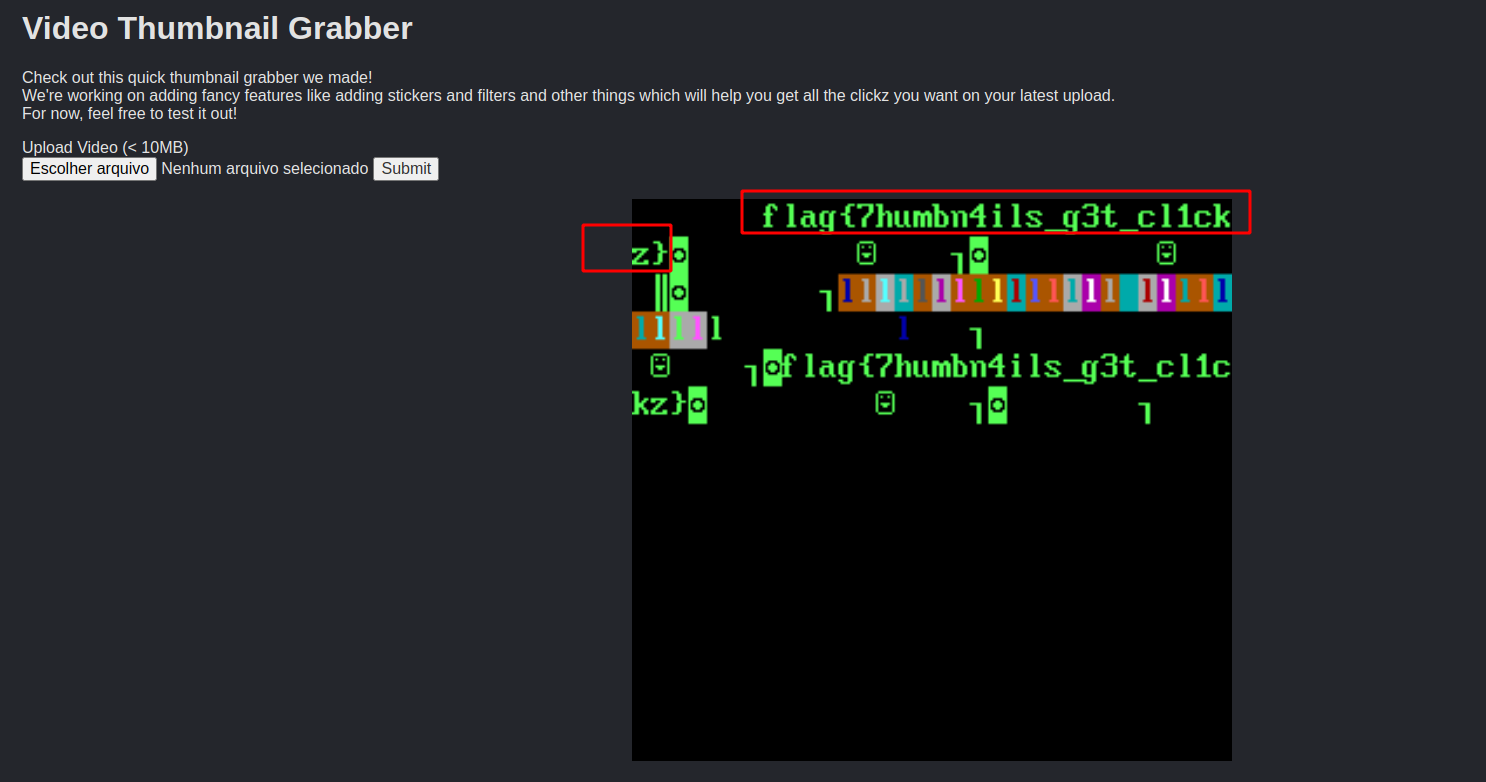
About the challenge
Basically, the challenge was a file upload feature that generates and shows a thumbnail
when you upload an mp4 file.
Looking at the source code, we can see the /uploads/ folder and a full path disclosure. Inside the /uploads/ folder there was a flag file, but it was not possible to access it directly.
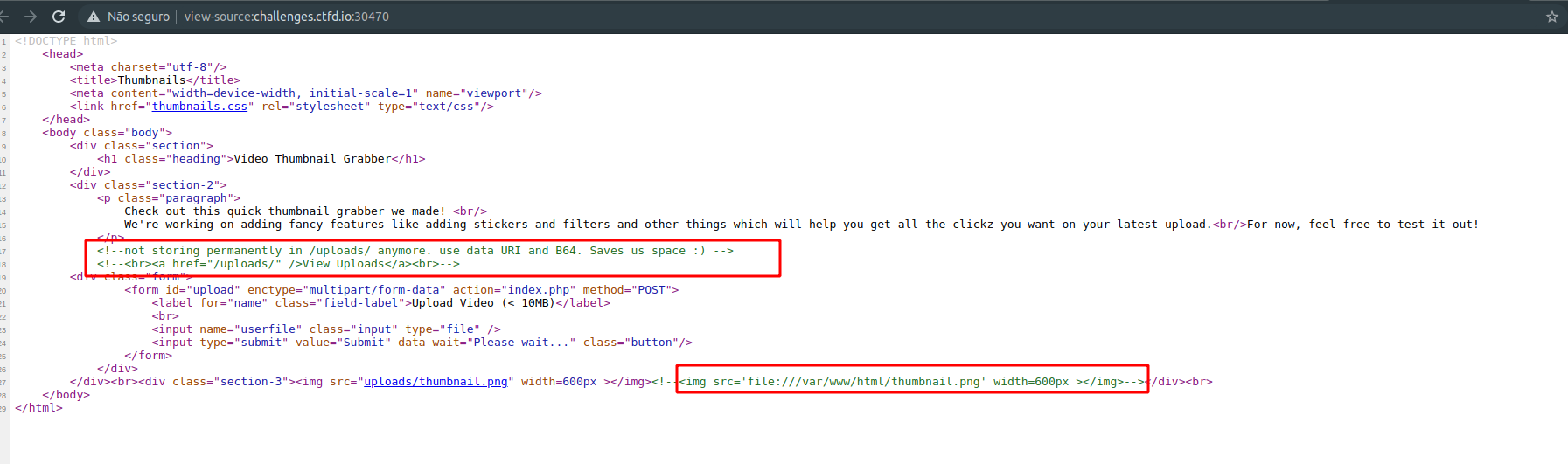
At this point it was clear that this was going to be an SSRF-style issue, but it wasn’t obvious how to reach the file. I tried to modify the base64 file handled by the upload process, but it didn’t work. After a while, a friend told me about SSRF using video files, so I started digging into that and found a BlackHat paper and some HackerOne reports.
Challenge solution
The idea was to abuse how the backend generates thumbnails from the video. Since we knew the full path to the flag file (from the path disclosure), we could craft a video that points to that local file.
Using the tool below, we inject a reference to the flag file into the video:
./gen_xbin_avi.py file:///var/www/html/uploads/flag.txt ~/Downloads/bla.mp4
After uploading the new mp4 file, the server processes it to generate a thumbnail
and ends up reading the local file we pointed to, leaking the flag.