[ Writeup ] TenableCTF - Thumbnail
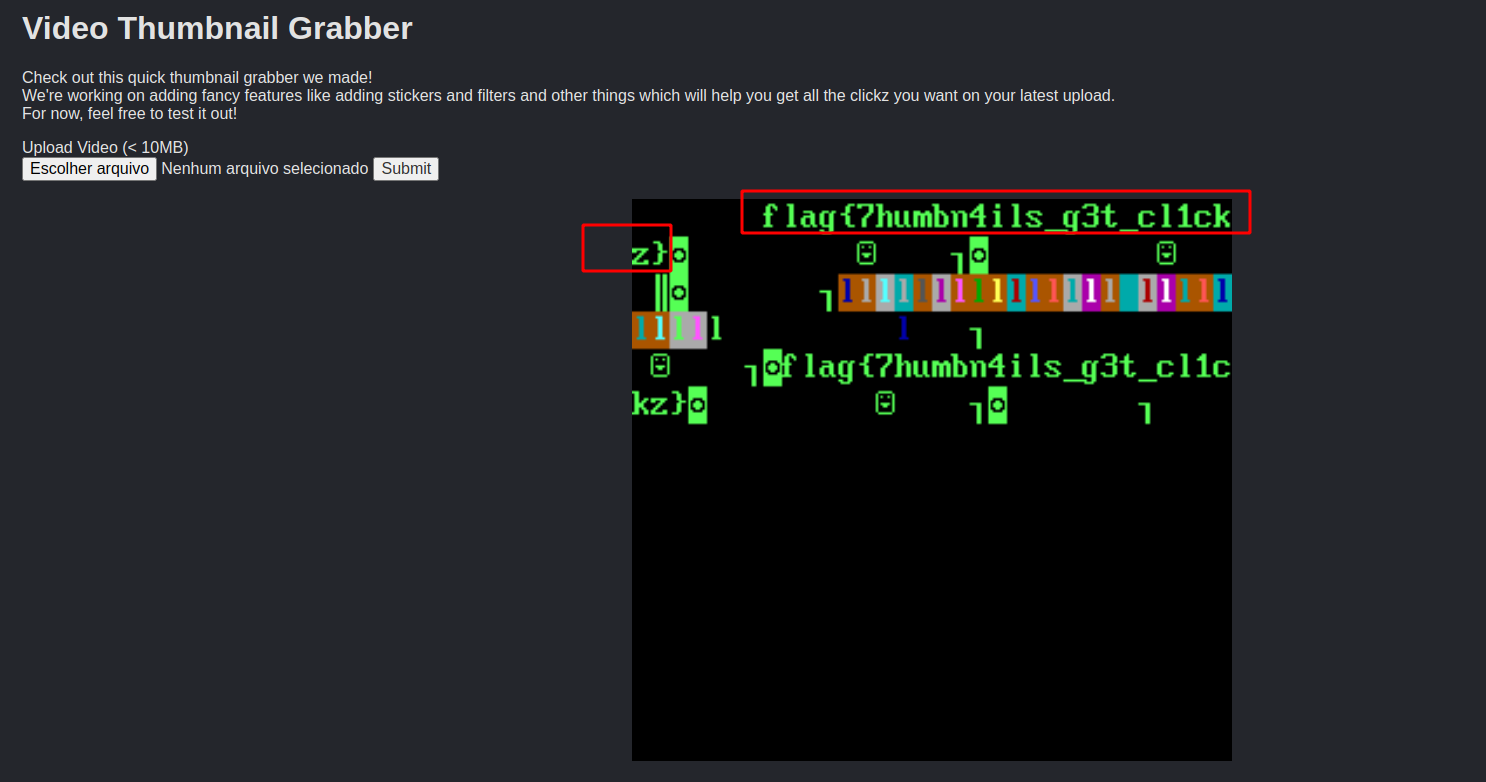
Basically the challenge is file upload which show the thumnail when you send a mp4 file.
Looking at the source code we can see the /uploads/ folder and a full path disclose. Into the /uploads/ folder had a flag file, but it was not possible to accesss it directly.
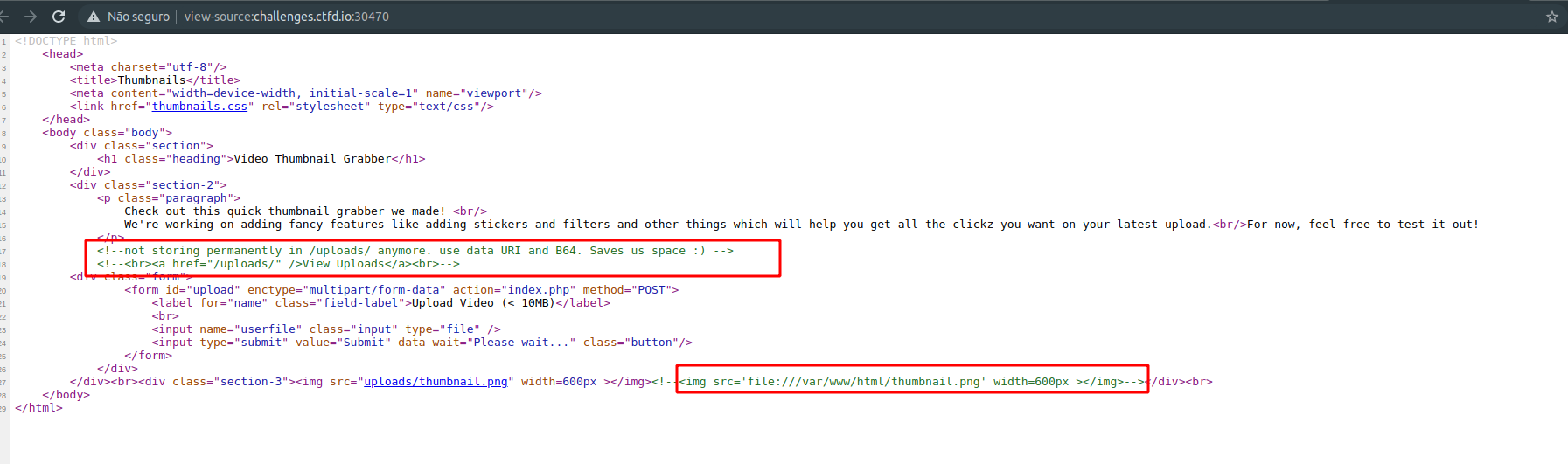
I knew it was a SSRF, but I didn't realize how to get this file. I tried to change the file via base64 generated by the upload, but it didn't work. After a while a friend told me about SSRF using video files, so I found a paper and some hackerone's reports.
So, I used a tool to insert the path to the flag file, once we already know the full path disclosed.
./gen_xbin_avi.py file:///var/www/html/uploads/flag.txt ~/Downloads/bla.mp4
After upload the new mp4 file we can get the flag.