What's GLPI?
GLPI is an ITSM software tool that helps you plan and manage IT changes in an easy way, solve problems efficiently when they emerge and gain legitimate control over your company’s IT budget and expenses.
Many companies use GLPI to manage their clients and tickets. GLPI has different kinds of users. To manage plugins the user needs to have a tech role. So if you steal this kind of account you can go to the administration page and dump the whole database to clone in your local lab.
The Vector
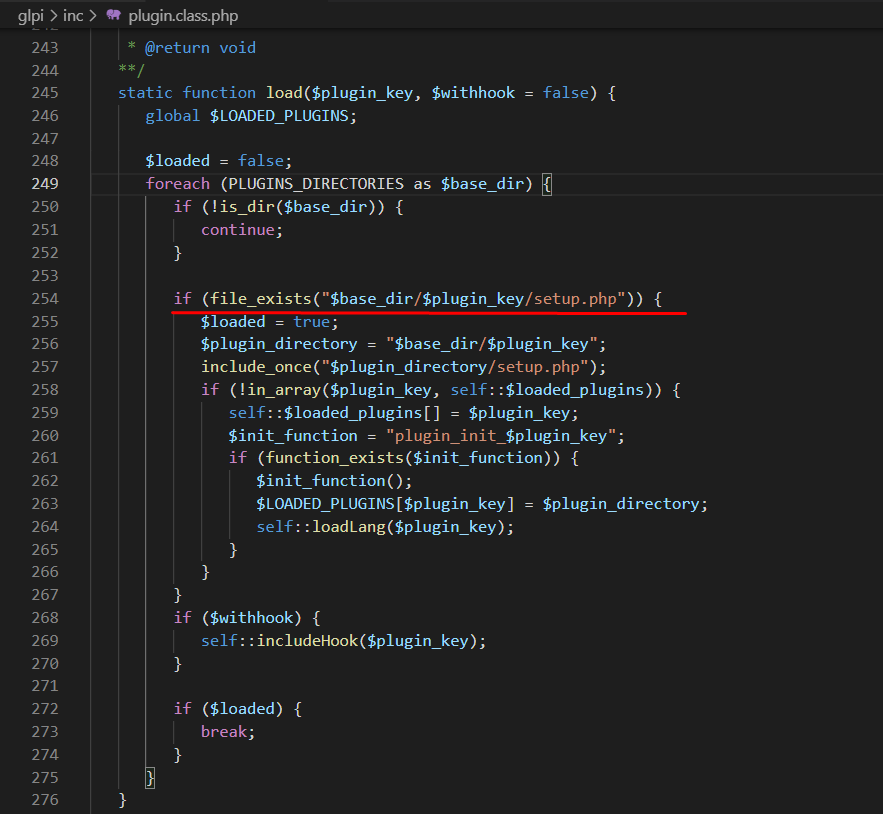
During the plugin installation process, GLPI reads the setup.php file from plugins to
show information such as author, plugin version, license, etc.
The problem here is simple: they do not validate and sanitize these information before rendering them to the user. Trusting user input is never a good idea.
GLPI loads the plugin using the setup.php file, as we can see in this piece of code:
setup.php file from plugins.
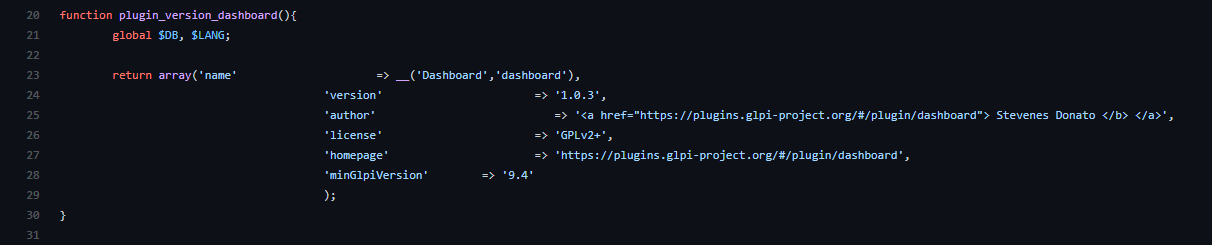
Plugins need to have a function called plugin_version_NAMEOFPLUGIN(). This function
returns an array that contains information such as version, author, license, homepage and the minimum GLPI version.
We saw this function at Fig.2.
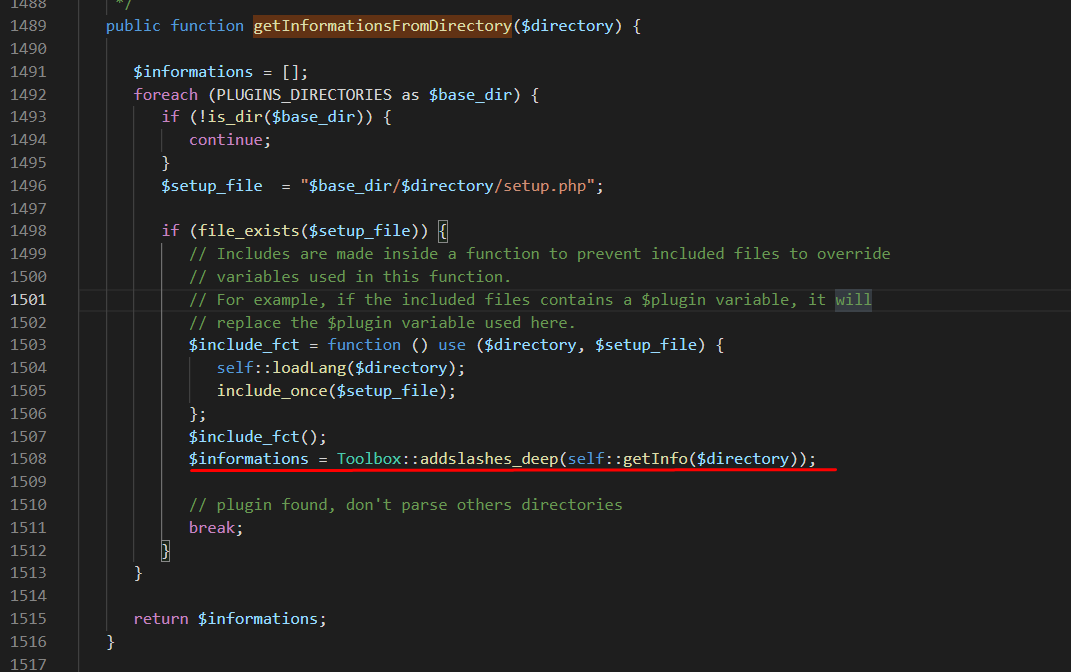
getInfo().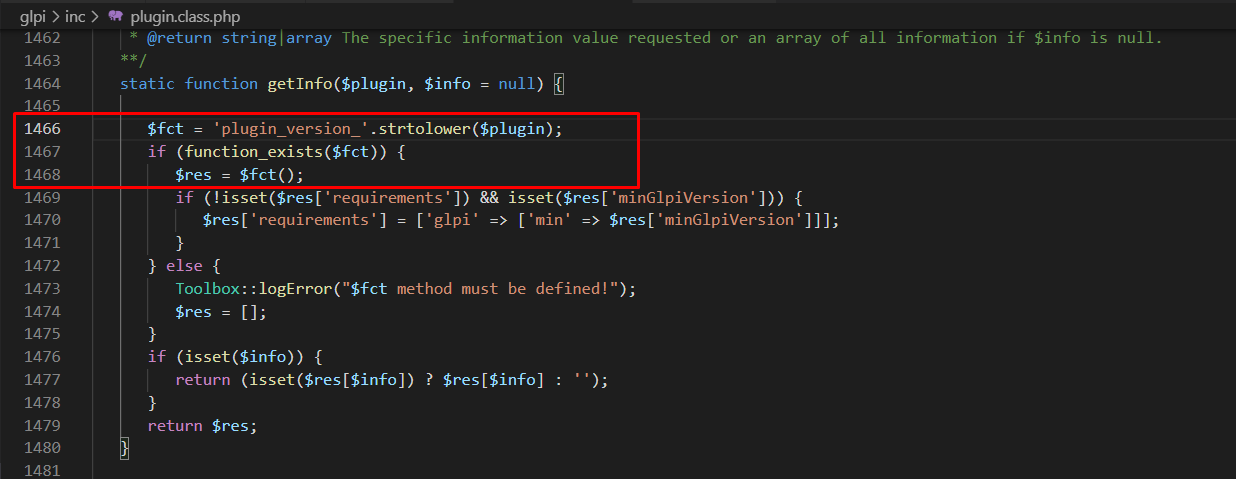
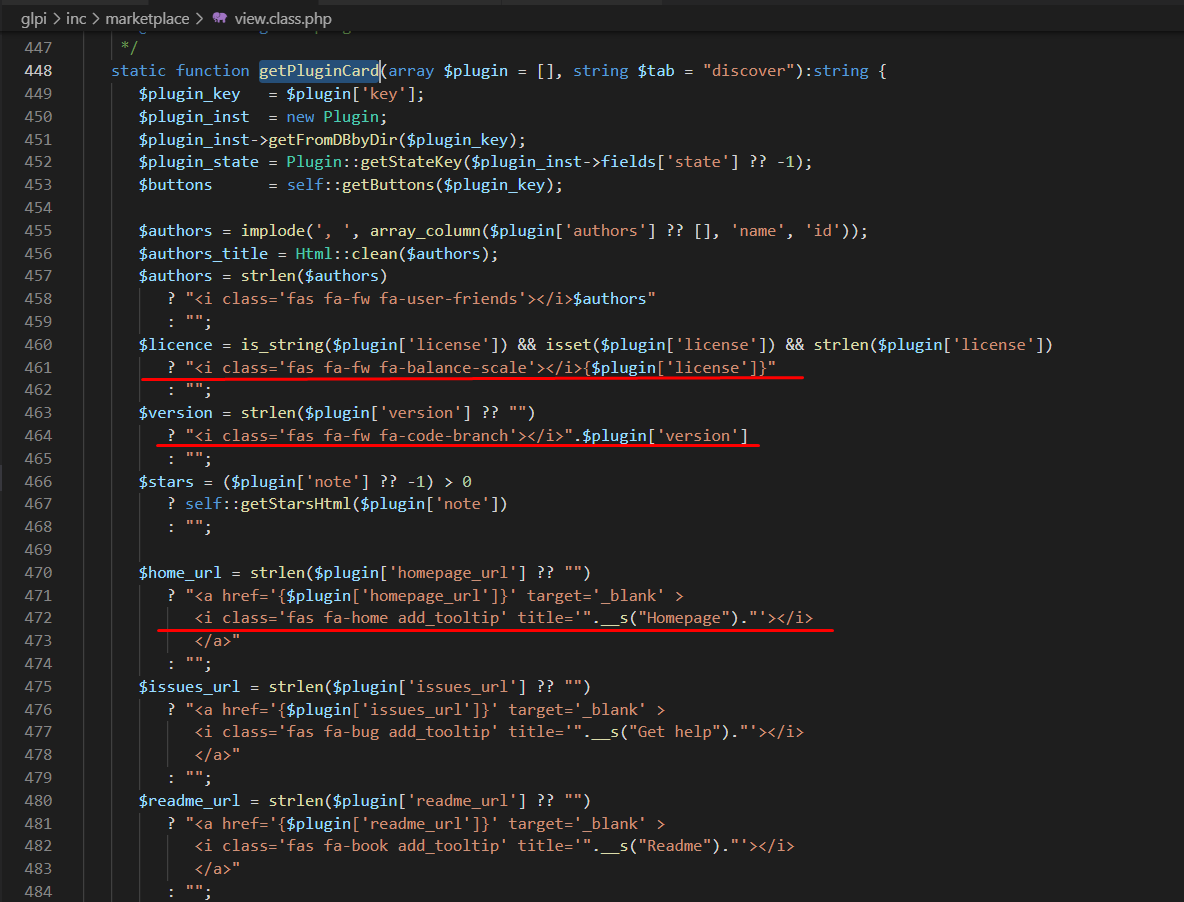
To display these information to the user, GLPI uses /front/plugin.php, which calls
view.class.php. As the following image shows, there is no escaping of HTML/JavaScript code.
All information is concatenated directly into HTML.
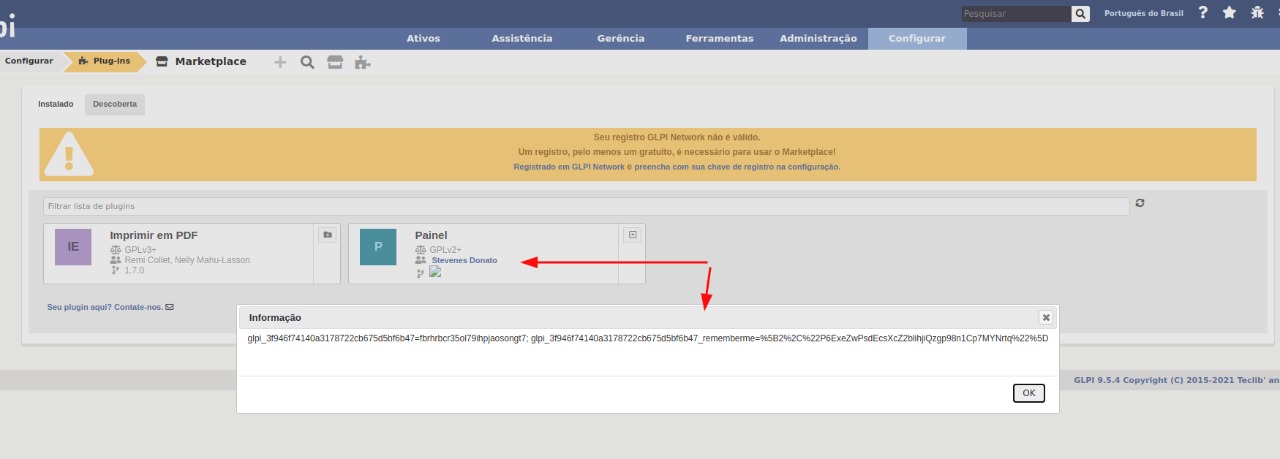
Here we can see the payload being executed: