CVE-2021-30144 - Information Disclose
GLPI Plugin - Dashboard <= 1.0.2
GLPI is an incredible ITSM software tool that helps you plan and manage IT changes in an easy way, solve problems efficiently when they emerge and allow you to gain legitimate control over your company’s IT budget, and expenses.
Many companies use GLPI to manage their clients and tickets. When the GLPI is well configured files and folders as glpi/files/_log/event.log and /files/_dumps are prohibited. The event.log file permits to enumerate users once it logs authentication activities.
Another positive point is that users with customer roles could not see the activities of other customers and users, unless the action is involved in their tickets.
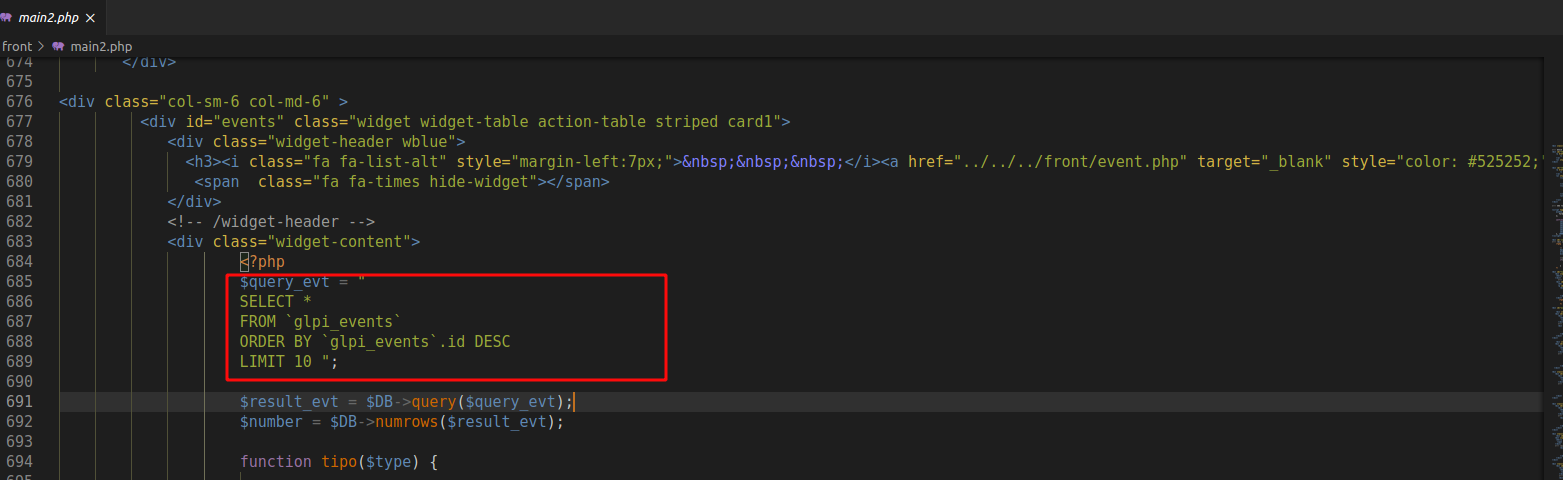
For this reason the plugin Dashboard created by stdonato is a good manner to bypass this protection. The plugin has some protections as check read permisions to protect some data, but the file main2.php doesn't check this permision and permits us to see "sensitive" informations as:
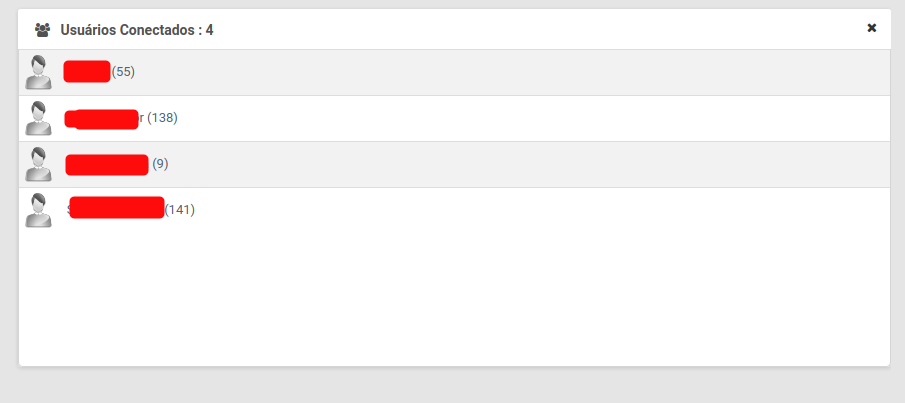
- Who is connected
- Users with Tech Roles (generally they have high privileges).
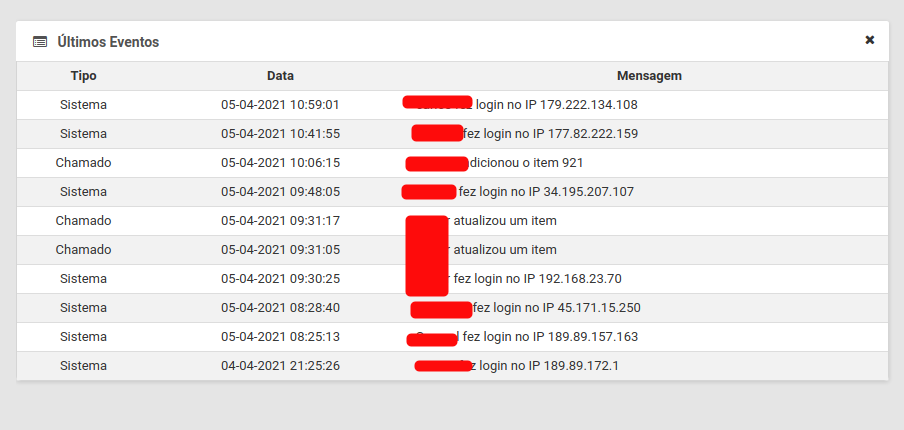
- Other Client authentication and some events.
- Last tickets from other clients.
- How many clients the application has.
All you need to access this file is a low profile. You can directly access this file into target.com/glpi/plugins/dashboard/front/main2.php
The reason of this flaw is really simple. The file checks if the user is authenticated but didn't check the user's permission.
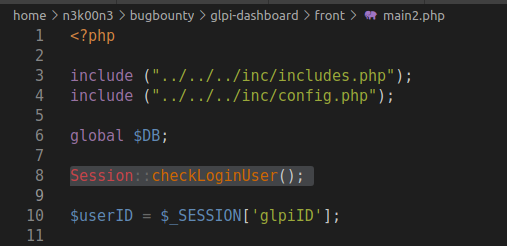
We also can see the how the plugin brings the information in the line 685.